Wednesday, April 28, 2010
बादशाह की अंगूठी
बादशाह ने शाही खजाना खोल कर जनता की तकलीफ दूर करने की कोशिश की पर धीरे - धीरे वह भी खाली हो गया। आखिरकार बादशाह ने राज्य के सभी प्रमुख लोगों की बैठक बुलाई , लेकिन कोई हल नहीं निकला। एक दिन दरबार में बादशाह ने अपनी अंगूठी निकाल कर खजांची को देते हुए कहा , ' इसे बेच दो। मेरे पास अब सूखा राहत के लिए कुछ नहीं बचा। '
दरबारियों में हलचल हुई। सब जानते थे कि बादशाह को अंगूठी बहुत प्यारी है। एक दरबारी ने कहा , ' थोड़ा इंतजार कर लीजिए। बारिश होने में अब कुछ ही दिन बाकी है। सब ठीक हो जाएगा। मगर ऐसी अंगूठी फिर नहीं मिलेगी। ' बादशाह ने कहा , ' ठीक कहते हो। मगर मैं बारिश के भरोसे लोगों को नहीं छोड़ सकता।
मुझसे जितना होगा मैं उनके लिए करूंगा। आम आदमी दुख सहता रहे और मैं अंगूठी का मोह करूं यह ठीक नहीं है। एक बादशाह का फर्ज है कि वह तकलीफ में लोगों का साथ दे। ' दरबारियों ने मौन होकर बादशाह के निर्णय का स्वागत किया और बादशाह का अनुकरण करते हुए उन्होंने भी अपने कीमती सामान बेच कर उसके पैसे सूखा राहत कोष में जमा करा दिए।
संकलन : सुरेश सिंह
Tuesday, April 27, 2010
प्रेम और भक्ति में हिसाब!
एक दिन वे उसे पास के शहर में भिक्षा मांगने ले गये। जब वे थक गये तो लौटते में एक बरगद की छांह बैठे, उसके सामने एक युवा दूधवाली दूध बेच रही थी, जो आता उसे बर्तन में नाप कर देती और गिनकर पैसे रखवाती। वे दोनों ध्यान से उसे देख रहे थे। तभी एक आकर्षक युवक आया और दूधवाली के सामने अपना बर्तन फैला दिया, दूधवाली मुस्कुराई और बिना मापे बहुत सारा दूध उस युवक के बर्तन में डाल दिया, पैसे भी नहीं लिये। गुरु मुस्कुरा दिये, शिष्य हतप्रभ!
उन दोनों के जाने के बाद, वे दोनों भी उठे और अपनी राह चल पडे। चलते चलते शिष्य ने दूधवाली के व्यवहार पर अपनी जिज्ञासा प्रकट की तो गुरु ने उत्तर दिया,
'' प्रेम वत्स, प्रेम! यह प्रेम है, और प्रेम में हिसाब कैसा? उसी प्रकार भक्ति भी प्रेम है, जिससे आप अनन्य प्रेम करते हो, उसके स्मरण में या उसकी पूजा में हिसाब किताब कैसा?'' और गुरु वैसे ही मुस्कुराये व्यंग्य से।
'' समझ गया गुरुवर। मैं समझ गया प्रेम और भक्ति के इस दर्शन को।
मन का राजा
भोज को उसके व्यवहार पर आश्चर्य हुआ। उन्होंने लकड़हारे को रोककर पूछा, ‘तुम कौन हो?’ लकड़हारे ने कहा, ‘मैं अपने मन का राजा हूं।’ भोज ने पूछा, ‘अगर तुम राजा हो तो तुम्हारी आमदनी भी बहुत होगी। कितना कमाते हो?’ लकड़हारा बोला, ‘मैं छह स्वर्ण मुद्राएं रोज कमाता हूं और आनंद से रहता हूं।’ भोज ने पूछा, ‘तुम इन मुद्राओं को खर्च कैसे करते हो?’ लकड़हारे ने उत्तर दिया, ‘मैं प्रतिदिन एक मुद्रा अपने ऋणदाता को देता हूं। वह हैं मेरे माता पिता। उन्होंने मुझे पाल पोस कर बड़ा किया, मेरे लिए हर कष्ट सहा। दूसरी मुद्रा मैं अपने ग्राहक असामी को देता हूं ,वह हैं मेरे बालक। मैं उन्हें यह ऋण इसलिए देता हूं ताकि मेरे बूढ़े हो जाने पर वह मुझे इसे लौटाएं।
तीसरी मुद्रा मैं अपने मंत्री को देता हूं। भला पत्नी से अच्छा मंत्री कौन हो सकता है, जो राजा को उचित सलाह देता है ,सुख दुख का साथी होता है। चौथी मुद्रा मैं खजाने में देता हूं। पांचवीं मुद्रा का उपयोग स्वयं के खाने पीने पर खर्च करता हूं क्योंकि मैं अथक परिश्रम करता हूं। छठी मुद्रा मैं अतिथि सत्कार के लिए सुरक्षित रखता हूं क्योंकि अतिथि कभी भी किसी भी समय आ सकता है। उसका सत्कार करना हमारा परम धर्म है।’ राजा भोज सोचने लगे, ‘मेरे पास तो लाखों मुद्राएं है पर जीवन के आनंद से वंचित हूं।’ लकड़हारा जाने लगा तो बोला, ‘राजन् मैं पहचान गया था कि तुम राजा भोज हो पर मुझे तुमसे क्या सरोकार।’ भोज दंग रह गए।
नीलम और पत्थर
जैसे -जैसे सूरज डूबने लगा , उसकी निराशा गहरी होती गयी । भगवान का नाम लेकर उसने एक बार और जाल डाला । पर इस बार भी वह असफल रहा . पर एक वजनी पोटली उसके जाल में अटकी । मछुआरे ने पोटली निकला और टटोला तो झुंझला गया और बोला -' हाय ये तो पत्थर है !' फिर मन मारकर वह नाव में चढा ।
बहुत निराशा के साथ कुछ सोचते हुए वह अपने नाव को आगे बढ़ता जा रहा था और मन में आगे के योजनाओं के बारे में सोचता चला जा रहा था । सोच रहा था 'कल दुसरे किनारे पर जाल डालूँगा । सबसे छिपकर ...उधर कोई नही जाता ....वहां बहुत सारी मछलियाँ पकड़ी जा सकती है ... । '
मन चंचल था तो फिर हाथ कैसे स्थिर रहता ? वह एक हाथ से उस पोटली के पत्थर को एक -एक करके नदी में फेंकता जा रहा था । पोटली खाली हो गयी । जब एक पत्थर बचा था तो अनायास ही उसकी नजर उसपर गयी तो वह स्तब्ध रह गया । उसे अपने आँखों पर यकीन नही हो रहा था , यह क्या ! ये तो ‘नीलम ’ था .
मछुआरे के पास अब पछताने के अलावा कुछ नही बचा था . नदी के बीचोबीच अपनी नाव में बैठा वह सिर्फ अब अपने को कोस रहा था ।
प्रकृति और प्रारब्ध ऐसे ही न जाने कितने नीलम हमारी झोली में डालता रहता है जिन्हें पत्थर समझ हम ठुकरा देते हैं।
Saturday, April 24, 2010
लालच का पिशाच
थोड़ा आगे बढ़ते ही उन्हें एक थैली पड़ी हुई मिली। उन्होंने थैली को खोलकर देखा। उसमें सोने की मोहरें थी। दोनों ने इधर-उधर निगाह दौड़ाई, वहां कोई भी नहीं था। प्रसन्न होकर बड़ा भाई बड़बड़ाया, 'हमारा काम बन गया। परदेस जाने की अब जरूरत नहीं रही।' दोनों को भूख लगी थी। बड़े भाई ने छोटे भाई से कहा, 'जाओ, पास के गांव से कुछ खाना ले आओ।' छोटे भाई के जाते ही बड़े भाई के मन में विचार आया कि कुछ ही समय में मोहरें आधी-आधी बंट जाएंगी। क्यों न छोटे भाई को रास्ते से ही हटा दिया जाए।
इधर छोटे भाई ने भी यही सोचा और उसने खाने में विष मिला दिया। वह खाने का समान लेकर लौटा तो बड़े भाई ने उसे गोली मार दी। छोटा भाई वहीं ढेर हो गया। बड़े भाई ने सोचा कि पहले खाना खा लूं, तब गड्ढा खोदकर भाई को उसमें गाड़ दूंगा। उसने ज्यों ही पहला कौर खाया, उसकी मौत हो गई। बूढ़े की बात सच निकली। लालच का पिशाच दोनों भाइयों को खा गया था।
Friday, April 23, 2010
Thank you Sun, for being there
‘‘Where does the Sun sleep?’’ the bright-eyed child asks her father. She and her family are celebrating Chhath on the Chowpatty seafront in Mumbai.
The winter festival of the setting Sun is so named because it falls on the sixth (chhath) day of Kartik, which comes just a week after the festival of lights.
The father, who’s been fasting the previous day, looks askance at the mother. But she just smiles as her daughter continues to clamour for an answer. The father would dearly love to fob off the child with a fanciful story about the Sun’s golden boat that’s supposed to be tethered under the horizon. But this would only open a new round of implacable questions.
Eventually, he decides to let in his daughter on the ‘secret’ of the rotating earth and the ever-awake Sun. But how does one explain that to a five-year-old in simple sound bytes? Then he gets a brainwave: Why not fall back on the age-old rationale of the Chhath festival itself as an explanation? ‘‘Bitiya, do you know why we observe Chhath ka parva – the festival of the sixth day?’’ he asks the child who shakes her head uncertainly.
‘‘On this occasion we thank the Sun for not sleeping ever and for giving us all the bounties of dhaan, dhan aur tan – crops, wealth and body or life itself. The Sun never sleeps. Being such a mighty star he does not need to rest ever,’’ the father explains further.
‘‘If he did, everything on earth would come to an end. Unlike him we do need to rest and sleep. So every evening, he seems to hide behind the Earth, who does a daily pradhakshina, a circumambulation around the star, just as we do out of gratitude and reverence.’’
Chhath is mainly viewed as a Bihari festival, and it is celebrated wherever people from Bihar have migrated to, whether in Mumbai or in Mauritius.
That Chhath is today celebrated across communities only enhances the essentially spiritual, ecological or even egalitarian dimensions of the festival. Chhath stands for thanksgiving to a star that is venerated in the Indian tradition as the only visible (pratyaksha) form of God, one that can be seen every day. Moreover, the Sun illuminates and sustains life not in a petty province or two but on a planetary scale. Hence the ancient rishis held it in high esteem as a manifest form of Brahmn: Asavodityo Brahmah, says the Rig Veda.
That also led them to an immensely popular cult based on the Gayatri Mantra. This is considered to be one of the most sacred universal practices that invoke the creative principle of the Sun in the form named Savitr.
The Chhath ceremonies however eschew deification, although there are attempts to overwrite its subaltern origins by connecting the ritual with the legendary Mahabharata hero Karna, the ‘son’ of Surya who was known for his valour and generosity.
Chhath also connects to the folk and rural roots of worshippers. The folk songs sung on the eve of Chhath are mainly in Maithili, Magadhi and Bhojpuri dialects that mirror the culture and social mores of Bihar, Uttar Pradesh and the terai regions.
In other respects Chhath is modern and inclusive. It appeals also to those who are uncomfortable with idol worship because it is a celebration of and a thanksgiving to the Sun for just being there, a great blaze in the sky.
Monday, April 19, 2010
आपसी विश्वास
संत कबीर रोज सत्संग किया करते थे। दूर-दूर से लोग उनकी बात सुनने आते थे। एक दिन सत्संग खत्म होने पर भी एक आदमी बैठा ही रहा। कबीर ने इसका कारण पूछा तो वह बोला, 'मुझे आपसे कुछ पूछना है। मैं गृहस्थ हूं, घर में सभी लोगों से मेरा झगड़ा होता रहता है। मैं जानना चाहता हूं कि मेरे यहां गृह क्लेश क्यों होता है और वह कैसे दूर हो सकता है?'
कबीर थोड़ी देर चुप रहे, फिर उन्होंने अपनी पत्नी से कहा, 'लालटेन जलाकर लाओ'। कबीर की पत्नी लालटेन जलाकर ले आई। वह आदमी भौंचक देखता रहा। सोचने लगा इतनी दोपहर में कबीर ने लालटेन क्यों मंगाई। थोड़ी देर बाद कबीर बोले, 'कुछ मीठा दे जाना।' इस बार उनकी पत्नी मीठे के बजाय नमकीन देकर चली गई। उस आदमी ने सोचा कि यह तो शायद पागलों का घर है। मीठा के बदले नमकीन, दिन में लालटेन। वह बोला, 'कबीर जी मैं चलता हूं।'
कबीर ने पूछा, 'आपको अपनी समस्या का समाधान मिला या अभी कुछ संशय बाकी है?' वह व्यक्ति बोला, 'मेरी समझ में कुछ नहीं आया।' कबीर ने कहा, 'जैसे मैंने लालटेन मंगवाई तो मेरी घरवाली कह सकती थी कि तुम क्या सठिया गए हो। इतनी दोपहर में लालटेन की क्या जरूरत। लेकिन नहीं, उसने सोचा कि जरूर किसी काम के लिए लालटेन मंगवाई होगी। मीठा मंगवाया तो नमकीन देकर चली गई। हो सकता है घर में कोई मीठी वस्तु न हो। यह सोचकर मैं चुप रहा। इसमें तकरार क्या? आपसी विश्वास बढ़ाने और तकरार में न फंसने से विषम परिस्थिति अपने आप दूर हो गई।' उस आदमी को हैरानी हुई। वह समझ गया कि कबीर ने यह सब उसे बताने के लिए किया था। कबीर ने फिर कहा,' गृहस्थी में आपसी विश्वास से ही तालमेल बनता है। आदमी से गलती हो तो औरत संभाल ले और औरत से कोई त्रुटि हो जाए तो पति उसे नजरअंदाज कर दे। यही गृहस्थी का मूल मंत्र है।'
Saturday, April 17, 2010
दूसरों के लिए
वह बादशाह की दुविधा को भांप गया। उसने बादशाह से कहा, 'आप सोच रहे होंगे कि मैं पागलपन का काम कर रहा हूं। जिस चीज से आदमी को फायदा नहीं पहुंचता, उस पर कौन मेहनत करता है, लेकिन यह भी सोचिए कि इस बूढ़े ने दूसरों की मेहनत का कितना लाभ उठाया है। दूसरों के लगाए पेड़ों के कितने फल खाएं हैं। क्या उस कर्ज को उतारने के लिए मुझे कुछ नहीं करना चाहिए? क्या मुझे इस भावना से पेड़ नहीं लगाने चाहिए कि उसके फल दूसरे लोग खा सकें? जो केवल अपने लाभ के लिए काम करता है, वह स्वार्थी होता है।' यह सुनकर बादशाह ने निश्चय किया कि वह प्रतिदिन एक पौधा लगाएगा।
Friday, April 16, 2010
ISDN Technology, Architecture Protocol, Device
ISDN Overview
What is ISDN?
The Integrated Services Digital Network (ISDN) is a set of international standards for access to advanced, all-digital public telecommunications networks. The key elements of this definition are:
- Integrated Services
- Voice
- Video
- Image
- Data
- Mixed media at a number of standard data rates
- Digital
- Digital terminal equipment
- Digital local loops
- Digital trunks
- Digital switching
- Digital signaling
- Network
- Worldwide, interoperating communications fabric under distributed control using common standards
ISDN standards have been defined by the ITU-T, a branch of the United Nations' International Telecommunications Union (ITU), in the series I and Q recommendations.
Integrated Services . . .
The current telephone network uses a mixture of analog and digital transmission methods and diverse access techniques and standards to provide different services:
- Switched voice telephony
- Centrex
- Dedicated point-to-point data carrier
- Packet-switched data carrier
- Dedicated point-to-point digital carrier
ISDN integrates all these services by providing a small set of standard interfaces and access protocols that apply to all services. Because ISDN is an international standard, the same interfaces and access protocols should be available anywhere in the world, across international boundaries, and among equipment from any set of vendors.
. . . Digital . . .
ISDN provides all of its services over an entirely digital transmission system. In pre-ISDN telephony, only interoffice trunks and certain high-capacity dedicated customer circuits use digital transmission.
ISDN employs digital transmission from the customer-premises equipment (CPE; i.e., telephones, data terminals, fax machines, etc.), through the local access loop , and across the carrier's trunk network. All central- and end-office switching is performed by digital switches, and all signalling (call establishment, "dial tone," ringing, on-hook/off-hook, service requests) occurs through digital protocols.
. . . Network
Finally, ISDN defines a NETWORK, not a loose collection of standards for private-line services. Ultimately, ISDN defines a single worldwide fabric of transmission and switching services operating under a common set of standards, with control distributed among all the various operating companies and national telecommunications authorities.
Components of ISDN
While individual operating companies and ministries will define the specific services, within the ISDN architecture the ITU standards define a number of component parts and functions:
- ISDN CHANNELS
- ACCESS TYPES
- DEVICES
- INTERFACES
- PROTOCOLS
ISDN Channels
A CHANNEL is the basic unit of ISDN service. The ISDN Standards define three basic types of channels:
- Bearer channels (B channels)
- Delta (or "Demand") channels (D channels)
- High-capacity channels (H channels)
B Channel
A B channel is a 64-Kbps unit of clear digital bandwidth. Based on the data rate required to carry one digital voice conversation, a B channel can carry any type of digital information (voice, data, or video) with no restrictions on format or protocol imposed by the ISDN carrier.
D Channel
A D channel is a signalling channel. It carries the information needed to connect or disconnect calls and to negotiate special calling parameters (i.e., automatic number ID, call waiting, data protocol). The D channel can also carry packet-switched data using the X.25 protocol.
The D channel is not a clear channel. It operates according to a well-defined pair of layered protocols:
- Q.921 (LAPD) at the Data Link Layer (Layer 2)
- Q.931 at the upper layers (Layers 3 and above)
Signalling on the D Channel
The ISDN D channel carries all signalling between the customer's terminal device and the carrier's end switching office.
Signalling information with end-to-end significance (i.e., which must be received by the terminal device at a call's destination, such as Automatic Calling Number Identification information) travels between the carrier's switching offices on the carrier's common-channel signalling network and on to the destination terminal through the receiving user's D channel.
H Channel
An H channel is a special, high-speed clear channel. H channels, designed primarily for full-motion color video, are not yet in common use. There are currently three kinds of H channel:
- H0 ("H-zero")
- H11 ("H-one-one")
- H12 ("H-one-two")
ISDN Access Types
ISDN offers two general types of access:
- BASIC RATE ACCESS (BRA)
- PRIMARY RATE ACCESS (PRA)
Basic Rate Access
Basic Rate Access is based on new technology conceived especially for ISDN. Designed to provide service to individual users or small businesses, Basic Rate Access provides two 64-Kbps B channels and one 16-Kbps D channel (referred to as 2B+D). In other words, it provides transmission facilities for one voice conversation (one B channel), one medium-speed data session (the other B channel), and the signalling exchanges needed to make them work (the D channel).
Two B channels at 64 Kbps plus one D channel at 16 Kbps equals 144K bps. The ISDN Basic Rate transmission protocol uses an additional 48 Kbps of bandwidth for maintenance and synchronization, so an ISDN Basic Rate Access actually uses 192 Kbps.
Primary Rate Access
Primary Rate Access, which is based on pre-ISDN digital carrier technology, is designed to provide high-capacity service to large customers for applications such as PBX-to-PBX trunking. There are two kinds of Primary Rate Access: 23B+D and 30B+D. Each depends on the kind of digital carrier available in a given country.
In North America and Japan, 23B+D Primary Rate Access operates at 1.544 Mbps and offers 23 B channels plus 1 64-Kbps D channel (usually located in time-slot 23), or 4 H0 channels, or 1 H11 channel. In most of the rest of the world, 30B+D Primary Rate Access operates at 2.048 Mbps and offers 30 B channels plus 1 64-Kbps D channel (located in time-slot 16), or 5 H0 channels, or 1 H12 channel.
ISDN Devices
In the context of ISDN standards, STANDARD DEVICES refers not to actual hardware, but to standard collections of functions that can usually be performed by individual hardware units. The ISDN Standard Devices are:
- Terminal Equipment (TE)
- Terminal Adapter (TA)
- Network Termination 1 (NT1)
- Network Termination 2 (NT2)
- Exchange Termination (ET)
Terminal Equipment (TE)
A TE is any piece of communicating equipment that complies with the ISDN standards. Examples include: digital telephones, ISDN data terminals, Group IV Fax machines, and ISDN-equipped computers.
In most cases, a TE should be able to provide a full Basic Rate Access (2B+D), although some TEs may use only 1B+D or even only a D channel.
Terminal Adapter (TA)
A TA is a special interface-conversion device that allows communicating devices that don't conform to ISDN standards to communicate over the ISDN.
The most common TAs provide Basic Rate Access and have one RJ-type modular jack for voice and one RS-232 or V.35 connector for data (with each port able to connect to either of the available B channels). Some TAs have a separate data connector for the D channel.
Network Termination (NT1 and NT2)
The NT devices, NT1 and NT2, form the physical and logical boundary between the customer's premises and the carrier's network. NT1 performs the logical interface functions of switching and local-device control (local signalling). NT2 performs the physical interface conversion between the dissimilar customer and network sides of the interface.
In most cases, a single device, such as a PBX or digital multiplexer, performs both physical and logical interface functions. In ISDN terms, such a device is called NT12 ("NT-one-two") or simply NT.
Exchange Termination (ET)
The ET forms the physical and logical boundary between the digital local loop and the carrier's switching office. It performs the same functions at the end office that the NT performs at the customer's premises.
In addition, the ET:
- Separates the B channels, placing them on the proper interoffice trunks to their ultimate destinations
- Terminates the signalling path of the customer's D channel, converting any necessary end-to-end signalling from the ISDN D-channel signalling protocol to the carrier's switch-to- switch trunk signalling protocol
ISDN Interfaces (Standard Reference Points)
The ISDN standards specify four distinct interfaces in the customer's connection to the network: R, S, T, and U.
From the standards viewpoint, these are not "real" physical interfaces, but simply STANDARD REFERENCE POINTS where physical interfaces may be necessary. However, in common practice, the names of reference points are used to refer to physical interfaces.
The R Interface
The interface at reference point R is the physical and logical interface between a non-ISDN terminal device and a terminal adapter (TA). The R interface is not really part of the ISDN; it can conform to any of the common telephone or data interface standards.
The S Interface
The interface at reference point S is the physical and logical interface between a TE (or TA) and an NT. The S interface uses four wires and employs a bipolar transmission technique known as Alternate Mark Inversion (AMI).
A special feature of the S interface is the "Short Passive Bus" configuration, which allows up to eight ISDN devices (TE or TA) to contend for packet access to the D channel in a prioritized, round-robin fashion. Only one device at a time can use a given B channel.
The T Interface
The interface at reference point T is the physical and logical interface between NT1 and NT2, whenever the two NTs are implemented as separate pieces of hardware. The specification for the T interface is identical to the specification for the S interface.
In most implementations, NT1 and NT2 exist in the same physical device, so there is no real T interface.
The U Interface
The interface at reference point U is the physical and logical interface between NT (or NT2) and the ISDN carrier's local transmission loop. It is also the legal demarcation between the carrier's loop and the customer's premises.
The U interface is implemented with two wires and uses a special quaternary signal format (i.e., four possible electrical states, with one pulse encoding a predefined combination of 2 bits) called 2B1Q. Quaternary encoding allows the U interface to carry data with a logical bit rate of 192 Kbps over a signal with a physical pulse rate of only 96 Kbps. The slower pulse rate is better suited to the less-predictable environment of the outside-plant loop carrier system.
ISDN Protocols
The ISDN protocols are signalling protocols that govern the exchange of data on the D channel. The two ISDN signalling protocols make up a layered protocol stack, with the Link Access Protocol for the D Channel (LAPD, also known as Q.921) providing Layer 2 data-link services and the Q.931 protocol providing higher-layer services.
LAPD is a simple, bit-oriented data-link protocol similar in structure and operation to HDLC and SDLC. The Q.931 signalling protocol is one of the most complex and feature-rich communication protocols ever designed.
LAPD (Q.921)
The LAPD protocol operates between TE and NT over the D channel of an ISDN S interface. In traditional data communications terms, the TE acts as DTE and the NT acts as DCE.
The unit of LAPD transmission is a FRAME. As in other bit- oriented protocols, frames are demarcated from an idle circuit and from other frames by a FLAG pattern. Like HDLC, LAPD can operate with either a Modulo 8 or a Modulo 128 frame window.
A LAPD frame contains the following fields:
- ADDRESS
- COMMAND/RESPONSE BIT
- CONTROL
- INFORMATION (only in frames carrying higher-layer data)
- FRAME CHECK SEQUENCE
LAPD vs. Other Bit-Oriented Protocols
The principal differences between LAPD and other bit-oriented protocols are the structure of the address field and the optional exchange of Sequenced Information (SI0 and SI1) frames.
- LAPD Address Field
- A LAPD address is 16 bits long and contains two parts: the SERVICE ACCESS POINT IDENTIFIER (SAPI) and the TERMINAL ENDPOINT IDENTIFIER (TEI). The SAPI identifies the specific service (i.e., voice, circuit- switched data, network management, etc.) to which the frame refers. The TEI identifies the TE itself, especially in situations such as Primary Rate Access or the Basic Rate Access short passive bus, where a single physical link might terminate at more than one TE.
- Sequenced INFORMATION Frames
- For applications that require a quicker response to frame errors than the normal MOD 8 or MOD 128 sequence numbering offers, LAPD provides a Sequenced Information service which uses a MOD 2 "frame window." Sequenced Information frames traveling in the same direction alternate between SI0 and SI1, reducing the LAPD frame window to one outstanding frame for special situations.
Q.931: The ISDN D-Channel Signalling Protocol
In fulfilling the ISDN goal of Integrated Services over common facilities, the Q.931 D-channel signalling protocol does much of the integrating. The principal job of Q.931 is to carry signalling information about the nature of the ISDN service required for specific calls (or data sessions) between the end user's terminal equipment and the ISDN carrier's end office.
The following is a short list of some critical information the Q.931 protocol MUST convey:
- SERVICE INFORMATION
- Information on the nature of the service requested for the call: voice, D-channel packet switched data, B-Channel packet switched data, circuit-switched data, electronic mail, facsimile, video, or others
- TERMINAL CAPABILITIES
- Information on the capabilities of the terminal equipment originating and receiving the call: the type of signalling required (i.e., stimulus signalling for simple digital telephones or functional signalling for full- featured ISDN terminals) and the terminal's ability to handle special features and services [e.g., Automatic Number Identification (ANI), ANI blocking, 800-service, call screening, call forwarding, data rate adaptation, conference calling]
- HANDSHAKING
- Negotiations between the originating and receiving terminals on the nature of information to be exchanged
In addition to these mandatory features, the Q.931 protocol must support the wide range of OPTIONAL features offered by all possible vendors of ISDN terminal and switching equipment. While ISDN provides a standard architecture and common interfaces, it necessarily leaves much room for invention, innovation, and just plain market differentiation among the products and services that implement the standard.
No single device supports the whole range of possible Q.931 messages. The ITU Q.931 standard provides only a minimally functional subset that allows different manufacturers and ISDN carriers to provide a rich variety of features and services.
To support this variety of features and functions, the Q.931 has several features of its own that make it a uniquely complex protocol:
- OPTIONAL FIELDS
- VARIABLE-LENGTH FIELDS
- CODESET SHIFTING
- PROTOCOL SHIFTING
- OPTIONAL FIELDS
- Most protocols offer some options in the structure of a message to allow for efficiency in ordinary operation (i.e., short packets for common functions). The Q.931 protocol provides a broad hierarchy of OPTIONAL fields whose appearance in a given message depends on the nature of the service requested, the nature of the terminal device, and sometimes even the specific application being served.
- VARIABLE-LENGTH FIELDS
- Most optional fields in Q.931 messages can vary in length. A Q.931 message can contain a large amount of information designed simply to allow terminal equipment to find specific fields in the message.
- CODESET SHIFTING
- Different national ISDNs, equipment vendors, and private carriers require special ways of encoding signalling information. The Q.931 protocol allows for shifting among several CODESETS to accommodate this variation.
- PROTOCOL SHIFTING
- Because the ISDN standards require that the D channel be able to carry packet-switched data as well as signalling information, the Q.931 protocol contains features that allow shifting into an entirely different protocol from message to message. These features take the form of a shift indicator that states that the rest of the current message should be interpreted as X.25 (or another alternative protocol).
Q.931 AND SS#7
The Q.931 protocol operates only on the D channel of the ISDN interface between the customer's terminal equipment and the ISDN carrier's Exchange Termination (ET). It does not provide end-to-end signalling over the public telephone network, although certain features of the protocol (such as terminal handshaking) do have end-to-end significance.
The carrier's ET locates those Q.931 messages that have end- to-end significance and translates them onto the carrier's own common-channel signalling network, which uses ITU Common Channel Signalling System Number 7 (SS#7) for signalling among end-office and central-office switches. At a call's destination end office, the ET retranslates end-to-end signalling information and adds it to the local signalling in the Q.931 data stream between the ET and the terminal equipment on the receiving end of the call.
Testing ISDN
Like any digital communications facility, ISDN can be tested at any of several levels. ISDN tests can operate strictly at the physical level, at the level of the logical transmission path, and at the higher levels of logical protocol. All of these tests can provide valuable information in testing ISDN circuits and equipment.
Physical Testing
PAIR QUALIFICATION is the most common reason for testing ISDN at the physical level. ISDN circuits must often use pre-ISDN local-loop facilities designed to carry more-robust analog transmissions. A high-speed digital transmission technique is sensitive to signal degradation from such common local-loop features as bridge taps and echo cancellers.
Before installing ISDN, carrier craftspeople must qualify the wire pairs to handle the ISDN signal. Purely physical parameters such as continuity, impedance, and electrical loading are especially important.
At a slightly higher level, digital tests such as Bit Error Rate and Error-Free Seconds Rate can be used to qualify the local loop.
Protocol Testing
There are four basic reasons for performing protocol tests on ISDN circuits:
- CONFORMANCE TESTING
- INTEROPERABILITY TESTING
- PERFORMANCE TESTING
- TROUBLESHOOTING
Conformance Testing
Conformance testing is designed to prove whether a given device, service, feature, or implementation of ISDN conforms to a specific standard. The standard may be the ITU I- and Q- series references or may be a carrier's or manufacturer's own technical reference.
Conformance tests are usually run automatically in long series of short, very specific tests with pass/fail results provided in stages along the way. Many ISDN providers, especially telecommunications ministries, require conformance testing before a given product or service can be operated on their networks. A given product or service is usually tested once for conformance.
Interoperability Testing
Interoperability testing is designed to prove whether two ISDN products or services (i.e., one vendor's terminal and another vendor's switch) can perform together according to specification. Any ISDN product needs to be tested for interoperability with any other ISDN product with which it may communicate.
A maxim in interoperability testing is that, "The commutative law does not apply." In other words, if A interoperates with B and B interoperates with C, A does not necessarily interoperate with C. ISDN products must be tested for conformance and interoperability at every major revision.
Performance Testing
Performance testing requires the gathering and display of statistics on the numbers of protocol units (i.e., frames, packets, messages) transmitted and received over time between units. The goal of performance testing is to discover deviations (from a specification or from normal operation) that point to underlying problems in the terminal or switching equipment or in the operation of the protocols themselves.
For ISDN, degrading performance of the D channel protocols (such as longer and longer Call Setup times) can indicate a number of protocol problems that ranges from user error at the terminal to traffic overloading on the carrier's network. Degrading data communications performance on a B channel might point to a failure to negotiate Calling parameters on the D channel.
In general, performance testing uncovers operational problems that might otherwise pass interoperability testing.
Troubleshooting
Once the user has determined that a problem has occurred on a circuit, troubleshooting finds the problem's cause. For ISDN circuits to date, the principal cause of circuit problems has been user error.
ISDN defines many new ways of performing familiar tasks (e.g., making a telephone call). Practices that were once common sense can now cause protocol problems.
Failure of terminal and switching equipment to interoperate properly despite passing interoperability tests is another major ISDN worry, especially in end-to-end signalling between similar but not identical terminals.
ISDN also adds a new layer of complexity to straightforward protocol testing of data communications over the B channels. Users must now look for subtle effects of D-channel Call Setup procedures, such as failure to complete the call over the D channel before link startup begins on the B channel.
Multichannel Protocol Monitoring
These descriptions of ISDN problems and testing techniques illustrate the need for multichannel protocol testing on ISDN circuits. Protocols on the D channel control much of what happens on the B channels, and events on the B channels can highlight protocol problems on the D channel.
In order to test ISDN properly, a protocol analyzer must be able to monitor at least the D channel and one of the B channels simultaneously. It should also be able to correlate events in time on the separate channels.
Monitoring and Emulation
An ISDN protocol analyzer should also be able to monitor on one channel and emulate on another.
Monitoring a B channel while simulating a Call Setup on the D channel allows an operator to see the intended (or unintended) results of D-channel actions on the B channel under control. Monitoring the D channel while emulating on a B channel can illustrate important signalling events, such as how the D channel responds to an abnormal termination on the B channel.
Multichannel Emulation
Emulating a switch or terminal device on both the D channel and a B channel allows the protocol analyzer to control an ISDN communication completely, both to verify normal operation and to test the effects of abnormal conditions. All conformance and interoperability testing of ISDN protocols should be performed as dual-channel emulations.
Additional Information
This document only gives a general overview of Integrated Systems Digital Networks. For more detailed information on ISDN standards and technologies, see the documents available from the Internation Telecommunications Union (ITU). For information on specific implementations, consult the manufacturers' or carriers' reference documents and technical advisories.
Saturday, April 10, 2010
जीने का उत्साह
महर्षि रमण के आश्रम के नजदीक किसी गांव में एक अध्यापक रहते थे। रोज के पारिवारिक तनाव से वह बहुत ज्यादा दुखी हो गए थे। अंत में उन्होंने इस अशांति से मुक्ति पाने की सोची, किंतु आत्महत्या करने का निर्णय लेना उन्हें इतना आसान नहीं लगा। मनुष्य को अपने परिवार के भविष्य के विषय में भी सोचना पड़ता है। इसी ऊहापोह में वह महर्षि रमण के आश्रम में पहुंचे।
महर्षि को प्रणाम कर वह बैठ गए। फिर कुछ देर बाद उन्होंने आत्महत्या के बारे में महर्षि की राय जाननी चाही। रमण उस समय आश्रमवासियों के भोजन के लिए बड़े मनोयोग से पत्तलें बना रहे थे। अध्यापक के सवाल पर उन्होंने कुछ खास नहीं कहा। अध्यापक महोदय उनके उत्तर की प्रतीक्षा करने लगे। उन्हें रमण का इस तरह पत्तल बनाना थोड़ा अटपटा लगा। उन्होंने साहस कर आखिर पूछ ही लिया, 'भगवन! आप इन पत्तलों को इतने परिश्रम से बना रहे हैं, लेकिन भोजन के बाद तो इन्हें कूड़े में फेंक ही दिया जाएगा।' महर्षि मुस्कराते हुए बोले, 'आप ठीक कहते हैं, लेकिन किसी वस्तु का पूर्ण उपयोग हो जाने के बाद उसे फेंकना बुरा नहीं है।
बुरा तो तब कहा जाएगा, जब उसका उपयोग किए बिना ही अच्छी अवस्था में उसे कोई फेंक दे। आप तो विद्वान हैं। मेरे कहने का तात्पर्य समझ ही गए होंगे।' इन शब्दों से अध्यापक महोदय की समस्या का समाधान हो गया। उनमें जीने का उत्साह आ गया और उन्होंने आत्महत्या का विचार त्याग दिया।
संकलन: लखविन्दर सिंह
संकट को जीवन की पाठशाला मानो
आदमी संकट के नाम से ही घबराता है। संकट का आभास होते ही वह उससे बचने के उपाय करने लगता है। लेकिन संसार में शायद ही कोई ऐसा हो जिसने संकटों का सामना न किया हो। लेकिन अपने संकटों से कोई व्यक्ति जितने अधिक सबक सीखता है, वह जीवन में उतना ही सफल होता है।
मार्क रदरफोर्ड एक बहुचर्चित लेखक थे। बचपन में एक दिन वे समुद्र के किनारे बैठे थे। दूर समुद्र में एक जहाज लंगर डाले खड़ा था। उनके मन में जहाज तक तैरकर जाने की इच्छा बलवती हो उठी। मार्क तैरना तो जानते ही थे, कूद पड़े समुद्र में और तैरकर उस स्थान तक पहुंच गए जहां जहाज लंगर डाले खड़ा था। लेकिन जब वापस लौटने के लिए किनारे की तरफ देखा तो निराशा हावी होने लगी, वह दूर, बहुत अधिक दूर लगा।
मार्क ने लिखा है -मनुष्य जैसा सोचता है, उसका शरीर भी वैसा ही होने लगता है। कुविचारों के कारण मैं, एक फुर्तीला किशोर, बिना डूबे ही डूबा हुआ-सा हो गया। लेकिन अपने विचारों को जब मैंने निराशा से आशा की ओर धकेला, तो चमत्कार-सा होने लगा। शरीर में नई शक्ति का संचार हो रहा था। मैं समुद्र में तैर रहा था और सोच रहा था कि किनारे तक नहीं पहुंचने का मतलब है डूबकर मरने से पहले का संघर्ष। मेरा बल मजबूत हुआ, मेरे अपने ही विचारों से। जैसे मुझे संजीवनी मिल गई। पहले मन में भय था और अब विश्वास किनारे तक पहुंचने की क्षमता का। अपने उस विचार के सहारे ही रदरफोर्ड वापस लौटकर किनारे तक पहुंचने में सफल हुआ। मार्क ने लिखा -बिना साहस के मंजिल नहीं मिलती। बिना विश्वास के संकट से उबरा नहीं जा सकता। जब डूबना ही है तो संघर्ष क्यों न करें।
विचार की शक्ति अणु से भी महान होती है। विचार ही तो है जो मनुष्य को संकट में डालता है या फिर संकट से उभारता है। विचार ही मनुष्य को नैतिक बनाता है या पतित करता है। विचार पहले, क्रिया बाद में। कार्लाइल ने संकट को अनुभव माना है और इसे पाठशाला की संज्ञा दी है। उसने उदाहरण दिया है -अखाड़े में उस्ताद अपने शिष्य को बार-बार पटकनी देकर गिराता है, उसे चोट भी लगती है, मोच भी आती है, शरीर से धूल लगती है, थकान होती है, लेकिन बार-बार की पटकनी से ही शिष्य वह सीख पाता है जिसके लिए वह अखाड़े में आता है। मनुष्य अपनी समस्या का समाधान दूसरों से चाहता है। दूसरे लोग सहयोगी बन सकते हैं, उपाय सुझा सकते है, पर समाधान नहीं कर सकते। समस्याओं का उत्स व्यक्ति स्वयं होता है। समाधान भी स्वयं से मिलता है।
मार्ग में अवरोध भी आ सकते हैं। उन्हें उत्साह और साहस के साथ पार करना होता है। कहीं अपमान मिलता है, कहीं निराशा का कुहासा सामने आता है, कहीं असफलता सहचरी के रूप में दिखाई देती है, इन स्थितियों का सम्यक विश्लेषण इनसे मुक्ति का मार्ग प्रशस्त कर सकता है। लेकिन उसके अभाव में तात्कालिक आवेश और अविचारित निर्णय व्यक्ति को पीछे भी धकेल सकता है।
अधिकांश मनुष्यों के दुर्भाग्य का मूल कारण यही होता है कि उन्हें अपने ऊपर भरोसा नहीं होता। वे अपने भाग्य को ही कोसने में अपना बहुमूल्य समय नष्ट कर देते हैं। जो व्यक्ति अपने को निर्बल और कमजोर समझता है उस व्यक्ति को कभी विजय नहीं मिल सकती। अपने को छोटा समझने वाला व्यक्ति इस संसार में सदा कमजोर समझा जाता है। उस व्यक्ति को कभी वह उत्तम पदार्थ नहीं मिल पाते जो सदैव यह कहकर अपने भाग्य को कोसता है कि वह पदार्थ मेरे भाग्य में नहीं था।
प्रस्तुति : ललित गर्ग
Thursday, April 8, 2010
What is Style?
What do you think about when you hear someone use the word “style”?
Whenever the term “style” is used, it most commonly refers to one’s fashion or outer appearance. But I want to remind you that style is much more than your shoulder length haircut, fashionable coat, or your Ferragamo shoes.
Style = Expression
It’s the total combination of the way you dress, talk, move your body, or do anything for that matter. Simply put, it’s how we express our inner being outwardly. This includes all of our thoughts, emotions, interests, and values. Everything on the outside is merely a reflection of what’s on the inside.
A lot of the people think that what I do is just help people transform their outer appearance. This is what they think of when they hear “style coach” or “image consultant,” and will come to me for a personal shopping session - wanting mainly to focus on fashion.
Although, I like to think of myself as a “self-expression coach,” because I firmly believe that fashion is just one part of your style.
Most of us aren’t aware of what we’re communicating most of the time - and it’s way beyond our reach to keep track of everything that we’re presenting. When we do find out through an outside source (usually to our disgust), whether through a close friend or relative, it seems far from the ideal vision that we have of ourselves. This is where a coach can come in and pinpoint all the factors that are contributing to what we don’t want, and how we can fix it.
For example, meet John Smith. He may seem like a nice guy who everyone loves, but when it comes to dating women, he says he just can’t seem to keep a woman attracted to him. What’s causing this? It could be a factor of many things he’s unaware of. The tone of his voice which is seeking validation, the fashion faux pas he’s making through his outfit combination, or some kind of insecurity in him that reveals itself through his mannerisms.
We all have things about ourselves we’d like to change just like John here. Once you identify your unattractive flaws or mannerisms, you’ll have the power to change it.
Some people think that because I’m a style coach I must be an unstoppable force of charisma who looks impeccable all the time. But sometimes I’m at home unshaven and wearing clothes that are more about comfort than fashion. I’m just a guy obsessed with the subject of style, and how we can improve every aspect of ourselves to be more effective in our interpersonal relationships. I love learning and analyzing this stuff, and while obsessively doing so I try to share what I learn because I love helping people more than anything else.
I firmly believe that every man has the capability to be charismatic - being the type of guy that everyone loves and is drawn towards. My life purpose is to continuously grow in this way and help others to bring this part of themselves out as well.
So what parts make up your complete “style?”
1. Your Reputation/Branding
Building a great self-brand or reputation is key to how much influence you’ll have in any setting. And I’m not talking about being a label junkie.
Guard your reputation above everything else, because once it’s tainted, it’s very hard to change people’s view of who you are.
For example, if you were introduced to a room full of people as being someone who won a Nobel prize for finding the cure to cancer, and someone who has brought a tremendous amount of medical aid to multiple third world countries, people will trust you more and whatever words you say to them will carry more credibility.
Compare that to me telling the room that you’re a psychopath, who just managed to get out of the county jail for murdering 23 people. You could say the nicest things and everyone will screen them through their current perception of you until you’ve convinced them otherwise.
People will believe anything about you at first, and then they’ll keep their eye on you to see if you’re for real. Then whatever information is consistent with their perception of you will get added to their current picture, whatever is not, will be changed or removed.
2. Clothing/Fashion sense
While what you wear isn’t going to make up your entire impression, it does make up over 80% of your first impression. What you wear is what will kick-start the impression you make on others before you even open your mouth. This is the place from which people will filter everything you say and do.
Just because style = expression doesn’t mean you can wear whatever you want while ignoring the message it’s conveying. There is a “language” that is spoken through specific types of clothing, that you must become familiar with in order to make a more positive influence than a negative one.
For example, picture a man in a well-fitted suit telling you that he runs a multi-national corporation and makes billions of dollars. Then, picture a man in an ill-fitting, dirty outfit telling you the same thing. Which would you believe more?
3. Your Grooming
Your grooming is part of your outer image that people will judge (most of the time subconsciously) to see how well you care for yourself. People tend to associate how well-groomed you are to the level of self-respect you have.
An example of this is the guy who has a fashionable hair cut that doesn’t have any stray hairs but is very well kempt, verses the guy who has an overdue haircut of a few weeks. Not only does the other man look more important and social, but he carries with him an image of more confidence and power.
We look at women the same way, when we compare the woman with straight silky hair against the woman with nappy hair that looks in need of a good conditioner and wash. I’m not looking down on anyone, but judgments are being made everyday from every single person whether consciously or not. Our brains are wired to make sense of everything around us through our senses, to calculate whether things are healthy or unhealthy, advantageous or harmful, etc.
4. Non-verbal
According to studies at the University of California, 93% of our communication is non-verbal. Imagine asking someone “How are you?” If that person replies “Fine” in a curt manner with a frown on their face, and their arms crossed, are they communicating that they really feel fine?
The messages we get across to other people has very little to do with the words that we use.
For example, what’s going to make you seem more like a confident and fun guy at a party? Standing around nursing a beer in your hand, and trying to look cool? Or goofing around, dancing like these guys, not caring what anyone thinks?
Besides body language, the tone, pitch, and volume we use in our voice is all part of non-verbal communication that is really at the heart of the words we use.
A person with a naturally loud voice can appear insensitive and domineering. There may also be insecurity issues at play, where the speakers feels they need to speak loudly to be listened to. A naturally soft-spoken person may be thought to be shy and insecure. They may think that what they have to say is not worth hearing - or at least this is the message that is getting across to others.
I found some funny clips of the show 30 Rock on the internet, which seems like a pretty funny show. Alec Baldwin does some great acting here of different voices and tones. We can tell exactly what kind of character he’s playing each time, even if we close our eyes and just listen to his tonality.
5. Your Lifestyle and Values
The way we live is all dependent on our values. If we value adventure, we may enjoy activities that involve a level of risk and fear such as skydiving, bungee jumping, or riding a roller coaster. On the other hand, if we value security, we may be reluctant to do such activities.
In the past, when I first focused starting on my style journey, I thought that people weren’t smart enough to figure out the real me if I just worked hard to mange their perception of who I am.
I soon realized that no matter how hard you pretend to be something you’re not, people will have enough information to piece together who you really are. No matter what you say, do, or try to orchestrate, something, somewhere, will reveal the truth.
There is no way around this and it’ll cost you less energy to actually work on becoming and being the person you want to be than pretending and trying to do. I’m reminded of a familiar saying that “We’re human beings, not human doings.”
Like in poker, there are always “tells.” Who you are on the inside will always manifest outwardly in some way. Even if you may not realize it, you can’t hide for that long.
Don’t underestimate the perceptiveness of others, if you are trying to be someone you’re not, people will see it clearly soon enough. Even through a tiny action regarding an insignificant thing, such as you holding the door for someone or the way you treat a baby, can tell someone more about you than a whole written autobiography can. There are things that we can’t possible think to manage that will make an impression on the people around us.
This is why it’s so important to work on who you are on the inside just as much as you do outward. This is what true “style” is.
Why Should You Want These Things at Your Best Level?
We all have an ideal vision of who we want to be. Whatever part of us that isn’t matching up to that ideal version of ourselves leaves room for us to grow. Only by being as close to this vision as possible, can we experience ultimate joy and fulfillment in our lives.
Happiness comes from self-esteem, and the better we become the more we like ourselves, affecting our confidence and creating an upward spiral towards limitless potential.
And the key is to continuously work on improving yourself, more than trying to manage the situations around you. You will attract into your life not necessarily what you want, but who you are.
Some Action Steps to Take
Here are some things you can do to set yourself on the path to your best style:
1. Create a folder of yourself and collect all your current pictures. Also, if you have a video camera, film yourself, and keep this file as well. This will give you tons of self-awareness which is the first step towards lasting change.
Do you remember the last time you watched yourself on camera? Were you ever surprised at the sound of your voice? The way you talked? Your facial expressions? Your poor posture? The best path to start your style improvement is to get an outside perspective.
2. Send the pictures you’ve collected to your friends and get some friends to send you some notes about what they would think about this guy if they didn’t know him. Would they think he was successful? Intelligent? Attractive to women? If you think you can pretend you’re someone else, looking at this guy for the first time, then write down everything you would assume about this guy.
3. Check the notes that you now have, are they in line with what you want to be communicating? Now that you’ve become aware of where you’re standing, decide where you’re going. What kind of person would you like to be? Write down how you want to world to understand you.
Start by surrounding yourself with people who have the values and characteristics you want for yourself, and model after them.
It’s imperative that you choose the people around you carefully, because you will start to become like them. Who we’re around on a consistent bases affects our thoughts, values, habits, and behaviors.
The good news it that these people you surround yourself don’t have to be alive or next to you in person. They can be there through books, tapes, video, etc.
So model after your favorite celebrities, ripped out ads from fashion magazines, or through friends you look up to.
4. Get a coach. A coach will pinpoint where you are and help you create an exact plan for where you want to go. Whatever it’s for (a sport, fashion, body building), a coach will save you a ton of time spent trying to figure out everything yourself.
5. Track your progress on our newly updated forums. Get advice and feedback from other guys who are on the same quest - to becoming their best selves.
Style development is parallel to personal development. Who you really are is close to the way the world will perceive you. But personal development is more for yourself, whereas style development is what will help you become more effective in your dealings with other people. Learning more and developing your competence on fashion, attractive body language, and social skills, it’ll result in a more fulfilling relationships with friends, coworkers, and the opposite sex.
Tuesday, April 6, 2010
Seven Tips on How to Get the Haircut You Want
The right hairstyle can give you self-confidence and satisfaction. Finding the right hairstyle for who you are does take a little effort though, but the results will be worth it in the end. As with any good relationship, the key to getting a great haircut is proper communication between you and your hairstylist. So before your haircut, you should have a consultation with your stylist during which time you should discuss various aspects of your hair and lifestyle. With that said, here are seven tips on how to get the haircut you want and deserve.
Do I Need a Matchmaking Service?
Finding a good stylist can be like searching for your next girlfriend. Ask around and find out which stylist or salon your friends use, or you can ask someone whose hair you admire. Perhaps you have seen a salon around town that looks cool and you’ve been wanting to give it a try. In this case I would call them up and ask if they specialize in a certain types of haircuts or styles. Would they consider themselves to be modern or classic in their attitude toward style? Edgy or conservative?
Don’t Be Shy
You might want to call or drop in a salon and ask if the stylists will give a free consultation before you make an appointment. Find out what their style is and the kind of cuts they are particularly good at cutting. Maybe they are better at certain types of styles than others or maybe they typically do women’s hair. It’s good to find these things out before they start whacking at your hair.
What’s Your Fuss Factor?
Let your stylist know how much time you spend on your hair. Maybe you aren’t fussy with your hair, or perhaps you only allow a certain amount of time for hair during your morning routine. Are you proficient with a blow-dryer, or do you prefer the natural route? What kinds of styling aids are you used to using?
What Do You Mean No Mohawks at the Office?
It’s also important for them to know what your lifestyle is like. Do you work in a conservative environment? Are you a man about town and fashion forward? Ultimately your stylist needs to know how comfortable you are wearing your hair. And make sure you're both on the same page when you get down to details. For example, your stylist may interpret "shaggy” or “shorter on the sides" much differently than you do.
I Didn’t Know My Hair Could Do That!
Make sure your stylist shows you how to best style your hair. Do they use the hairdryer in a particular way? What kind of products did they use in your hair? If your stylist doesn't explain what he/she is doing, don't hesitate to ask for an explanation of a technique or term they use. Understanding the language or terminology is key.
Lights, Camera . . .
A picture is worth a thousand words and a great way to start the conversation. The stylist I have interviewed say that more and more male clients are bringing in photos from magazines and such. With photos your stylist will be able to assess how suitable the cut you like is for your hair, your face shape and lifestyle. They can also suggest alternatives if it's not the perfect cut for you.
Money Money Money
Tip appropriately or you may not want your stylist to have a pair scissors near your face the next time you drop in. A Proper tip is 15% to 20% for your stylist & $5 for the person who washes your hair, if someone other than your stylist is doing so.
Saturday, April 3, 2010
दोषी कौन
किसी सेठ के यहां कई कर्मचारी काम करते थे। प्राय: सभी आलसी और कामचोर थे, केवल किरीट बेहद ईमानदार और मेहनती था। वह अपना काम करने के अलावा दूसरों के बचे कार्यों को भी पूरा कर देता था।
एक दिन सेठ ने अपने कर्मचारियों को बुलाया और कहा, 'मुझे पता चला है कि कुछ लोग अपना काम ठीक से नहीं कर रहे हैं। इससे व्यापार में घाटा हो रहा है। कामचोर कर्मचारी जल्दी सुधर जाएं अन्यथा उन्हें इसका नतीजा भुगतना होगा।' सेठ की चेतावनी से कुछ तो सुधर गए लेकिन ज्यादातर ने चेतावनी अनसुनी कर दी। किरीट हमेशा की तरह पहले अपने काम पूरे करता फिर अपने निठल्ले साथियों की मदद में जुट जाता।
कुछ दिनों के बाद सेठ ने फिर सभी को बुलाकर कहा, 'मैंने पहचान लिया है कि तुम लोगों में असली कामचोर कौन है। उसके खिलाफ कड़ी कार्रवाई होगी।' सभी कर्मचारी सोचने लगे कि आज पता नहीं किसकी नौकरी जाएगी। कुछ देर की चुप्पी के बाद सेठ ने कहा, 'सबसे बड़ा गुनहगार किरीट है। उसे सजा मिलेगी।' कर्मचारियों को समझ में नहीं आया कि सेठ क्या कह रहे हैं। एक ने कहा, 'सेठ जी, आप क्या कह रहे हैं।
किरीट तो सबसे ज्यादा मेहनती है।' सेठ ने कहा, 'तुम ठीक कहते हो। मेहनती और ईमानदार होना तो ठीक है, लेकिन दूसरे को आलसी बनाना ठीक नहीं है। दोषी वही नहीं होता जो कामचोर है बल्कि वह भी उतना ही दोषी है जो कामचोर लोगों के काम को पूरा करके उन्हें और निकम्मा बनाने में मदद करता है।' सभी कर्मचारी लज्जित हो गए। उन्होंने एक साथ कहा, 'सेठ जी, हम समझ गए कि आप हमसे क्या कहना चाहते हैं। हम आप को वचन देते हैं कि आज के बाद आप को कोई शिकायत नहीं मिलेगी।' उसके बाद सभी कर्मचारी मन लगाकर काम करने लगे। किरीट को दूसरों के काम करने की जरूरत ही नहीं पड़ती थी।
संकलन : सुरेश सिंह
Reporting & analyzing bugs:Problem Report
The point of writing Problem Report is to get bugs fixed.
To write a fully effective report you must:
1. Explain how to reproduce the problem:
programmers dismiss reports of problems that they can’t see for themselves.
2, Analyze the error so you can describe it in a minimum number of steps.
Reports that contain unnecessary steps make the problem look less general than it is.They also confuse and intimidate the reader. A programmer is more likely to postpone dealing with a report that look long and involved.
3. Write a report that is complete, easy to understand, and non-antagonistic.
A report that confuses or irritates the programmer doesn’t motivate her to fix it.
Friday, April 2, 2010
Synchronous Modems
Synchronous modems operates in the audio domain, at rates up to 28800 bps in audio lines, used in telephones systems (using synchronous data). The usual modulation methods are the phase modulation and integrated phase and amplitude (at higher rates than 4800 bps).
In synchronous modems, equalizers are used, in order to offset the misfit of the telephone lines. These equalizers are inserted in addition to the equalizers, that sometimes already exist in the telephone lines.
These equalizers an be classified into three main groups:
- Fixed/statistical equalizer - these equalizers offset the signal according to the average of the known attenuation in each frequency. Tuning the equalizer is sometimes done in the factory and stays fixed, usually they are used to operate at low rates in a dial up line.
- Manually adjusted equalizer - these equalizers can be tuned to optimal performance to a given line. These equalizers should be re-tuned when the line is replaced and periodically. Specially, it should be tuned frequently when the line is of a low quality and it's parameters are changed frequently. Tuning is done using a button inside the modem (or on the external board).
- Automatic equalizer - these equalizers are tuned automatically when the connection is established. Depending on the line quality in a specific moment, in a process of about 15ms to 25ms, after the first tuning, the equalizer samples the line continually and adjusts itself to the changed conditions, so the modem operates at each moment under optimal conditions. The fitness process operates, in some modems, at rates of 2400 times in a second.
Synchronous modems operate in the same manner asynchronous modems. However, synchronous modems operates at higher rates and since the requirements to transmit at these rates is increasing, most of the innovations are implemented for synchronous modems.
In synchronous modems the channel can be split for several consumers at various speeds. Modems who have this ability are called SSM - Split System Modem. These modems can use a simple split or a split using multipoint connection.
Synchronous data is accompanied by a clock signal. Synchronous data is almost always grouped in blocks, and it is the responsibility of the data source to assemble those blocks with framing codes and any extra bits needed for error detecting and/or correcting according to one of many different protocols (BISYNC, SDLC, HDLC, etc.). The data source and destination expect the modem to be transparent to this type of data, conversely, the modem can ignore the blocking of the data.
Asynchronous Modems
Most of the modems that operate in slow and moderate rates, up to 1800 bps, are asynchronous (using asynchronous data). Asynchronous modems operate in FSK modulation and use two frequencies for transmission and another two for receiving. Asynchronous modems can be connected in different options to the communication media:
- Using 2-wire or 4-wire interface.
- Using switched lines or leased lines.
- Using interface to call unit/automatic answer, when dialing-up.
In a 2-wire line, full duplex operation can be achieved by splitting the channel into two sub-channels.l
Asynchronous data is not accompanied by any clock, and the transmitting and receiving modems know only the nominal data rate. To prevent slipping of the data relative to the modems' clocks, this data is always grouped in very short blocks (characters) with framing bits (start and stop bits). The most common code used for this is the seven-bit ASCII code with even parity.
USART
The USART is a full-duplex synchronous/asynchronous receiver-transmitter proven in high-volume devices from National Semiconductor and available exclusively from IPextreme as synthesizable IP.
The USART supports a wide range of software programmable baud rates and data formats and operates in either Synchronous or Asynchronous (UART) mode. It implements automatic parity generation and several error detection schemes. The USART is capable of detecting a wakeup pattern to selectively enable the receiver and implements flow control logic for hardware handshaking.
The host interface of the USART complies with the AMBA 2.0 APB protocol. Control registers within the USART provide CPU control of baud rate, frame format, wakeup pattern detection, operating mode, and enabling/disabling interrupts. Status registers provide interrupt and error status. In addition, there are registers that hold the transmit/receive data.
In Asynchronous (UART) mode, the USART communicates with other devices using two signals: transmit (TDX) and receive (RDX). In Synchronous mode, the USART communicates with other devices using three signals: transmit (TDX), receive (RDX), and clock (CKX); data bits are transferred synchronously with the CKX signal. Flow control is available in both Asynchronous and Synchronous modes through RTS/CTS signaling.
To reduce chip-level pin count, the USART interface signals can be shared with other on-chip functions through a General Purpose I/O (GPIO) Controller.

FEATURES
- Full-duplex double-buffered receiver/transmitter
- Synchronous operation using the CKX clock pin
- CKX can be generated internally or externally
- Asynchronous (UART) operation
- Programmable baud rate between CLK/2 and CLK/32768 baud
- Programmable frame formats
- 7, 8, or 9 data bits
- 1 or 2 stop bits
- Odd, even, mark, space, or no parity
- Hardware support of parity-bit generation during transmission and parity-bit check during reception
- Software-controlled break transmission and detection
- Interrupt on transmit buffer empty, receive buffer full, receive error, and delta clear-to-send (flow control mode) conditions, each with a separate interrupt enable
- Internal diagnostic capability
- Automatic error detection
- Parity error
- Framing error
- Data overrun error
- 9-bit Attention mode
- DMA support for transmit and receive with separate enables
- Hardware flow control functions
- Clear-to-send (CTS)
- Request-to-send (RTS)
- Wakeup pattern detection according to ISO14230/KWP2000
- Debug support: Freeze/suspend USART activity
INTERFACES
- AMBA 2.0 APB host interface
- 8-bit read/write data buses
- 10-bit address bus
- USART pins (CKX, TXD, RXD, CTS, RTS) through chip I/O pads (optionally through a GPIO Controller )
- DMA interface
- One transmit DMA channel
- One receive DMA channel
- Clock interface
- APB clock for registers, DMA, interrupt functions, and for baud rate generation in Asynchronous mode
- Baud rate clock input for Synchronous mode with external baud rate generation
- Baud rate clock output for Synchronous mode with internal baud rate generation
- Interrupt interface (four interrupts)
- One asynchronous reset input
- Freeze/suspend interface
- DFT signals
HARDWARE CONFIGURATION OPTIONS
GATE COUNT AND PERFORMANCE
Gate count and maximum frequency depend on synthesis tool and target technology. Example values for a typical 130-nm technology are:
- 2300 (NAND2 equivalent) gates
- 100 MHz (APB clock)
DELIVERABLES
The USART is available in Source and Encrypted products. The Source product is fully configurable and is delivered in plain text Verilog source code. The Encrypted product, which is available in the Core Store, offers limited configurability (default parameter values) and is delivered in encrypted source code. Both products include:
- Synthesizable Verilog source code (encrypted in the Encrypted product)
- Integration testbench and tests
- Documentation
- Automatic configuration through the IPextreme IP distribution and support portal
- Scripts for simulation and synthesis with support for common EDA tools
USART-processor
A universal asynchronous receiver/transmitter is a type of "asynchronous receiver/transmitter", a piece of computer hardware that translates data between parallel and serial forms. UARTs are commonly used in conjunction with other communication standards such as EIA RS-232.
A UART is usually an individual (or part of an) integrated circuit used for serial communications over a computer or peripheral device serial port. UARTs are now commonly included in microcontrollers. A dual UART or DUART combines two UARTs into a single chip. Many modern ICs now come with a UART that can also communicate synchronously; these devices are called USARTs (universal synchronous/asynchronous receiver/transmitter).
 Definition
Definition
- The 8251A is a programmable serial communication interface chip designed for synchronous and asynchronous serial data communication.
- It supports the serial transmission of data.
- It is packed in a 28 pin DIP.
- Read/Write control logic
- Transmitter
- Receiver
- Data bus buffer
- Modem control.
The functional block diagram of 825 1A consists five sections. They are:
Read/Write control logic:
- The Read/Write Control logic interfaces the 8251A with CPU, determines the functions of the 8251A according to the control word written into its control register.
- It monitors the data flow.
- This section has three registers and they are control register, status register and data buffer.
- The active low signals RD, WR, CS and C/D(Low) are used for read/write operations with these three registers.
- When C/D(low) is high, the control register is selected for writing control word or reading status word.
- When C/D(low) is low, the data buffer is selected for read/write operation.
- When the reset is high, it forces 8251A into the idle mode.
- The clock input is necessary for 8251A for communication with CPU and this clock does not control either the serial transmission or the reception rate.
Transmitter section:
- The transmitter section accepts parallel data from CPU and converts them into serial data.
- The transmitter section is double buffered, i.e., it has a buffer register to hold an 8-bit parallel data and another register called output register to convert the parallel data into serial bits.
- When output register is empty, the data is transferred from buffer to output register. Now the processor can again load another data in buffer register.
- If buffer register is empty, then TxRDY is goes to high.
- If output register is empty then TxEMPTY goes to high.
- The clock signal, TxC (low) controls the rate at which the bits are transmitted by the USART.
- The clock frequency can be 1,16 or 64 times the baud rate.
Receiver Section:
- The receiver section accepts serial data and convert them into parallel data
- The receiver section is double buffered, i.e., it has an input register to receive serial data and convert to parallel, and a buffer register to hold the parallel data.
- When the RxD line goes low, the control logic assumes it as a START bit, waits for half a bit time and samples the line again.
- If the line is still low, then the input register accepts the following bits, forms a character and loads it into the buffer register.
- The CPU reads the parallel data from the buffer register.
- When the input register loads a parallel data to buffer register, the RxRDY line goes high.
- The clock signal RxC (low) controls the rate at which bits are received by the USART.
- During asynchronous mode, the signal SYNDET/BRKDET will indicate the break in the data transmission.
- During synchronous mode, the signal SYNDET/BRKDET will indicate the reception of synchronous character.
MODEM Control:
- The MODEM control unit allows to interface a MODEM to 8251A and to establish data communication through MODEM over telephone lines.
- This unit takes care of handshake signals for MODEM interface.
Transmitting and receiving serial data
The Universal Asynchronous Receiver/Transmitter (UART) controller is the key component of the serial communications subsystem of a computer. The UART takes bytes of data and transmits the individual bits in a sequential fashion. At the destination, a second UART re-assembles the bits into complete bytes. Serial transmission of digital information (bits) through a single wire or other medium is much more cost effective than parallel transmission through multiple wires. A UART is used to convert the transmitted information between its sequential and parallel form at each end of the link. Each UART contains a shift register which is the fundamental method of conversion between serial and parallel forms.
The UART usually does not directly generate or receive the external signals used between different items of equipment. Typically, separate interface devices are used to convert the logic level signals of the UART to and from the external signaling levels.
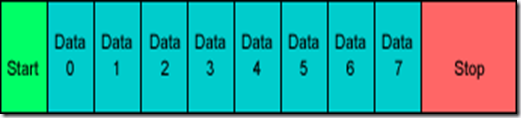
Asynchronous receiving and transmitting
In asynchronous transmitting, teletype-style UARTs send a "start" bit, five to eight data bits, least-significant-bit first, an optional "parity" bit, and then one, one and a half, or two "stop" bits. The start bit is the opposite polarity of the data-line's idle state. The stop bit is the data-line's idle state, and provides a delay before the next character can start. (This is called asynchronous start-stop transmission). In mechanical teletypes, the "stop" bit was often stretched to two bit times to give the mechanism more time to finish printing a character. A stretched "stop" bit also helps resynchronization.
The parity bit can either make the number of "one" bits between any start/stop pair odd, or even, or it can be omitted. Odd parity is more reliable because it assures that there will always be at least one data transition, and this permits many UARTs to resynchronize.
In synchronous transmission, the clock data is recovered separately from the data stream and no start/stop bits are used. This improves the efficiency of transmission on suitable channels since more of the bits sent are usable data and not character framing. An asynchronous transmission sends no characters over the interconnection when the transmitting device has nothing to send—only idle stop bits; but a synchronous interface must send "pad" characters to maintain synchronism between the receiver and transmitter. The usual filler is the ASCII "SYN" character. This may be done automatically by the transmitting device.
USART chips have both synchronous and asynchronous modes.
Asynchronous transmission allows data to be transmitted without the sender having to send a clock signal to the receiver. Instead, the sender and receiver must agree on timing parameters in advance and special bits are added to each word which are used to synchronize the sending and receiving units.
The start bit is always a 0 (logic low), which is also called a space. The start bit signals the receiving DTE that a character code is coming. The next five to eight bits, depending on the code set employed, represent the character. In the ASCII code set the eighth data bit may be a parity bit. The next one or two bits are always in the mark (logic high, i.e., '1') condition and called the stop bit(s). They provide a "rest" interval for the receiving DTE so that it may prepare for the next character which may be after the stop bit(s).
Modems
A modem (modulator-demodulator) is a device that modulates an analog carrier signal to encode digital information, and also demodulates such a carrier signal to decode the transmitted information. The goal is to produce a signal that can be transmitted easily and decoded to reproduce the original digital data. Modems can be used over any means of transmitting analog signals, from driven diodes to radio.
INTRODUCTION
The need to communicate between distant computers led to the use of the existing phone network for data transmission. Most phone lines were designed to transmit analog information - voices, while the computers and their devices work in digital form - pulses. So, in order to use an analog medium, a converter between the two systems is needed. This converter is the MODEM which performs MODulation and DEModulation of transmitted data. It accepts serial binary pulses from a device, modulates some property (amplitude, frequency, or phase) of an analog signal in order to send the signal in an analog medium, and performs the opposite process, enabling the analog information to arrive as digital pulses at the computer or device on the other side of connection.
Modems, in the beginning, were used mainly to communicate between DATA TERMINALS and a HOST COMPUTER. Later, the use of modems was extended to communicate between END COMPUTERS. This required more speed and the data rates increased from 300 bps in early days to 28.8bps today. Today, transmission involves data compression techniques which increase the rates, error detection and error correction for more reliability.
In order to enable modems of various types and different manufacture to communicate, interface standards were developed by some standard organizations
Today's modems are used for different functions. They act as textual and voice mail systems, facsimiles, and are connected or integrated into cellular phones and in notebook computers enabling sending data from anywhere. The future might lead to new applications. Modem speeds are not expected to be increased much over today's 28.8 kbps. Further dramatic speed increases will require digital phone technology such as ISDN and fiber optic lines.
New applications might be implemented such as simultaneous voice and data. Videophones are an example of this.
The modems can be classified according to their characteristics:
- Range
- Short Haul
- Voice Grade (VG)
- Wideband
- Line Type
- Dial-up
- Leased
- Private
- Operation Mode
- Half Duplex
- Full Duplex
- Simplex
- Synchronization
- Asynchronous
- Synchronous
- Modulation
- AM
- FM/FSK
- PM
- TCM
- Data Rate
Example:
The most familiar example is a voiceband modem that turns the digital data of a personal computer into analog audio signals that can be transmitted over a telephone line, and once received on the other side, a modem converts the analog data back into digital.
Types Of Modems:
1) External modems: It is the second term we have to consider from different types of computer modem. An External modem can be used to the same purpose and in the same conditions as internal computer modem. However external modem is a small box that uses other kind of interfaces to be connected to the computer.
2) USB modem: It could be a serial modem, named thus because it uses the serial port to connect to the computer. Usually installed on the back of the computer, the serial port is an easy-to-install option for the external modem. The same small box, on the other hand, can be an USB modem which normally uses USB port usually placed on the back or in front of the computer.
3) Dial-Up modem: First of all external modem can be a Dial-Up modem but more expensive than the internal.
As well as another type of external modem you may consider two important types of modem: cable modem and DSL modem if you need high-speed internet services. All ISPs usually supply a specialized modem named digital modem in the broadband package.
It’s important to notice that cablemodem has to connect to an Ethernet card, placed on the computer PCI slot to provide a broadband internet connection to the user. This is true if you opt to use Ethernet connection. However you won't need it if your option goes to use an USB connection.
4) Cable modem. The cable modem uses a coaxial cable television lines to provide a greater bandwidth than the dial-up comuter modem. An extremely fast access to the Web is providing by the cable modem with downstream transmission up to 38 Mbits/s and an upstream transmission up to 1 Mbits/s.
Unfortunately this transmission rate fluctuates with the number of users because of the shared bandwidth on which the cable technology is based.
5) DSL modem. DSL (Digital Subscriber Line) modem is exclusively used for connections from a telephone switching office to the user. This technology, available and frequently usable, split up into two main categories:
6) ADSLor Asymetric Digital Subcriber Line is used in North America and supports from 1.5 Mbits/s up to 9 Mbits/s of downstream transmission rate and up to 3 Mbits/s of upstream transmission rate.
7) SDSL. SDSL or Symetric Digital Subcriber Line is used in Europe and has the same data rates for downstream and upstream transmission which is 128 Kbits/s.
Radio modems
Direct broadcast satellite, WiFi, and mobile phones all use modems to communicate, as do most other wireless services today. Modern telecommunications and data networks also make extensive use of radio modems where long distance data links are required. Such systems are an important part of the PSTN, and are also in common use for high-speed computer network links to outlying areas where fibre is not economical.
Even where a cable is installed, it is often possible to get better performance or make other parts of the system simpler by using radio frequencies and modulation techniques through a cable. Coaxial cable has a very large bandwidth, however signal attenuation becomes a major problem at high data rates if a digital signal is used. By using a modem, a much larger amount of digital data can be transmitted through a single piece of wire. Digital cable television and cable Internet services use radio frequency modems to provide the increasing bandwidth needs of modern households. Using a modem also allows for frequency-division multiple access to be used, making full-duplex digital communication with many users possible using a single wire.
Wireless modems come in a variety of types, bandwidths, and speeds. Wireless modems are often referred to as transparent or smart. They transmit information that is modulated onto a carrier frequency to allow many simultaneous wireless communication links to work simultaneously on different frequencies.
Broadband
ADSL modems, a more recent development, are not limited to the telephone's voiceband audio frequencies. Some ADSL modems use coded orthogonal frequency division modulation (DMT).
Cable modems use a range of frequencies originally intended to carry RF television channels. Multiple cable modems attached to a single cable can use the same frequency band, using a low-level media access protocol to allow them to work together within the same channel. Typically, 'up' and 'down' signals are kept separate using frequency division multiple access.
New types of broadband modems are beginning to appear, such as doubleway satellite and power line modems.
Broadband modems should still be classed as modems, since they use complex waveforms to carry digital data. They are more advanced devices than traditional dial-up modems as they are capable of modulating/demodulating hundreds of channels simultaneously.
Many broadband modems include the functions of a router (with Ethernet and WiFi ports) and other features such as DHCP, NAT and firewall features.
Mobile modems and routers
T-Mobile Universal Mobile Telecommunications System PC Card modem------------------------------>
<--------CDMA2000 Evolution-Data Optimized USB wireless modem
Modems which use mobile phone lines (GPRS, UMTS, HSPA, EVDO, WiMax, etc.), are known as cellular modems. Cellular modems can be embedded inside a laptop or appliance, or they can be external to it. External cellular modems are datacards and cellular routers. The datacard is a PC card or ExpressCard which slides into a PCMCIA/PC card/ExpressCard slot on a computer.
The best known brand of cellular modem datacards is the AirCard made by Sierra Wireless. (Many people just refer to all makes and models as AirCards, when in fact this is a trademarked brand name.)Nowadays, there are USB cellular modems as well that use a USB port on the laptop instead of a PC card or ExpressCard slot. A cellular router may or may not have an external datacard (AirCard) that slides into it. Most cellular routers do allow such datacards or USB modems. Cellular Routers may not be modems per se, but they contain modems or allow modems to be slid into them. The difference between a cellular router and a cellular modem is that a cellular router normally allows multiple people to connect to it (since it can route, or support multipoint to multipoint connections), while the modem is made for one connection.